Rejecting the "Security Theater": Wallet Security is Entering the Era of Verifiability
Source: OKX
By 2025, Web3 will enter a new stage of "larger scale, higher-frequency usage," and wallets will accelerate their evolution from a "coin storage tool" to a chain-entry and transaction operating system. Market research firm Fortune Business Insights estimates that the cryptocurrency wallet market will reach around $12.2 billion in 2025 and may grow to $98.57 billion by 2034.
User-side expansion is also evident: a16z crypto estimated in the "State of Crypto 2025" that there are approximately 40-70 million active crypto users, with about 716 million crypto asset holders who "hold assets but may not necessarily be active on-chain"; Crypto.com Research's report also states that the global crypto holders increased from 681 million in the first half of 2025 to 708 million.
On the flip side of the increasing scale and penetration rate is the simultaneous amplification of security risks. It is no longer just about "whether the smart contract has vulnerabilities" but about intercepting risks at the user's critical points, such as clicking on links, connecting wallets, signing authorizations, and processing transactions.
In the on-chain world, the "attack surface" often extends beyond smart contract vulnerabilities and is more commonly related to low-barrier phishing, fake domains, impersonation of customer service, and authorization fraud as "pre-transaction risks." For example, Chainalysis defines "crypto drainers (wallet emptiers/phishing authorization tools)" as tools that do not steal account passwords but instead deceive users into connecting their wallets and approving malicious transaction authorizations, allowing assets to be drained directly. Public data also shows that in 2024, losses related to "wallet drainers" were close to the $500 million mark.
Therefore, enhancing the security of Web3 wallets will no longer focus solely on whether smart contracts have vulnerabilities but will need to pay further attention to how to proactively intercept risks at key user behavior points, known as "pre-transaction security."
In such an industry context, "security" is becoming increasingly challenging to address with a simple slogan but instead resembles a governance capability that needs continuous validation: whether it can be verified, whether it can be traced, and whether it can be disclosed in a timely manner are becoming important criteria for users in choosing a wallet.
From "Security Claims" to "Understandable Security Capability List"
For a long time, when wallet projects discussed security, common rhetoric included "we have undergone audits," "we have a whitepaper," and "we focus heavily on risk management." However, with the industrialization of scams and phishing, this "security claim" is losing its persuasiveness. The moment users truly encounter issues often happens in very brief interactions such as clicking on links, connecting wallets, and signing authorizations. The "crypto drainers" described by Chainalysis are a typical path: attackers disguise themselves as a legitimate page, guide users to complete authorization, and then transfer the assets; their research even mentions cases of forging Magic Eden pages and carrying out malicious transactions targeting Ordinals users.
Public data is also driving the industry narrative towards "understandability." Security Week, citing Scam Sniffer's statistics, reported that in 2024, nearly $500 million in losses were caused by wallet emptiers, with over 332,000 victims. These types of events do not require attackers to breach complex systems but rather rely more on users not understanding the risks during interactions. On the other hand, Chainalysis, in its 2025 disclosure, estimated that in 2024, on-chain scam revenue was at least $9.9 billion and could increase as more addresses are identified. When the main risk comes from the "user-side readability gap," wallet manufacturers must shift security from backend engineering to front-facing expression.
As a result, more and more wallets in the industry are starting to "productize" their security capabilities: they no longer just tell you "we are secure" but break down protective actions into a list that users can understand—such as which tokens will be flagged as high risk, which transactions will trigger alerts, which addresses or DApps will be blocked, and why the blocking is happening. The essence of this change is to transform security from a "qualification narrative" to an "interaction narrative": enabling users to receive actionable information before signing, rather than having to look at an audit PDF afterwards.
Following this trend, the newly launched and upgraded Security Center page of the OKX wallet provides a more typical example of "expressing in a list format." The page explicitly outlines three "frontline defenses" aimed at users: Token risk detection, Transaction monitoring, and Address screening, and explains their functions in a single sentence each, such as "Flagging high-risk tokens to reduce exposure to honeypots and bad actors," "Cross-chain real-time monitoring to identify suspicious on-chain activities," and "Intercepting interactions with malicious DApps and addresses." The benefit of this approach is that even if users do not understand security terminology, they can quickly relate to the action they are currently taking—whether to click, sign, or transfer.
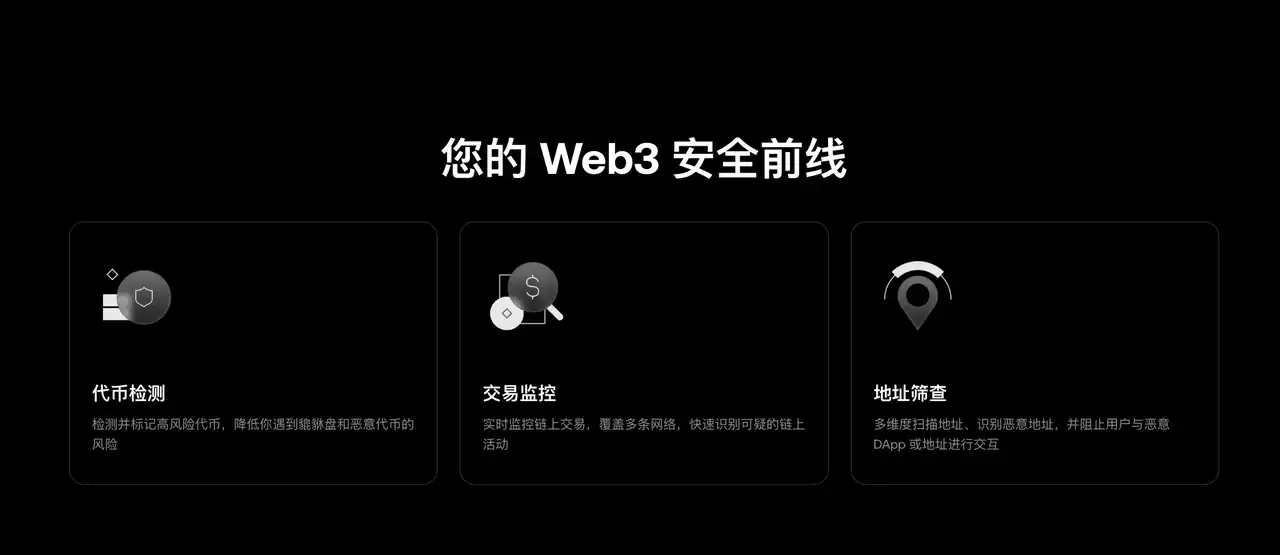
Click to visit: OKX Wallet Security Landing Page Audit Report
More importantly, "understandability" does not mean "talking to oneself." On the same page, the OKX wallet also provides an "View audit reports" link, connecting the "capability list" with "third-party verification." Furthermore, the audit report collection page in its help center further elaborates on the audit scope, number of issues found, and repair status, allowing users to transition from "understanding capabilities" to "verifying evidence" when needed.

This kind of transition from "security claim" to "understandable checklist" is not about making security sound grander, but about making security more actionable: as fraud increasingly relies on deception and disguise, whether a wallet can place risk alerts at interaction points, explain in user-friendly language "where the danger lies, why it's dangerous, and what you should do," is becoming part of security capability and increasingly determines whether users will stumble at a crucial step.

Audit Information "Publicly Verifiable": Transforming Third-Party Endorsement from "Linked" to "Verifiable Evidence Chain"
In the wallet industry, audits have long faced a practical problem: many projects have indeed "undergone audits," but the information is scattered across announcements, PDFs, and social media reposts, making it difficult for ordinary users to quickly understand "who audited it, what was audited, whether any issues were fixed, and when was it last updated." This time, the more prominent action by the OKX wallet is to consolidate publicly available third-party audit reports into a unified portal and directly indicate on the page "published on November 11, 2022, updated on November 17, 2025," allowing users to quickly determine at a glance that this is not just a one-time showcase but an ongoing information disclosure window that is actively maintained.

From the entries publicly displayed on this collection page, the scope of disclosure has not only focused on the traditional audit target of "smart contracts." Taking CertiK's entry dated May 23, 2024, as an example, the audit content clearly covers key code paths on the mobile end and frontend: including iOS/Android components, frontend ReactJS UI components, JS controllers interacting with the keyring, and multiple wallet SDK modules, while also providing the audit methodology and conclusion criteria.
In the same page, SlowMist's entry is closer to the "new paradigm" of wallet evolution in the past two years—auditable objects such as AA smart contract accounts, MPC keyless wallets, Ordinals transaction modules are all listed; in addition, audit information on the "private key security module" is separately presented, stating directly "private keys or mnemonic phrases are only stored on the user's device and are not transmitted to external servers," responding to the user's core concerns about key security with clearer boundary descriptions.
The value of this "centralized display" is not only in having more comprehensive information but, more crucially, in binding "new capabilities" with "verifiability" at the same entry point: as the wallet industry increasingly moves towards complex architectures such as AA and MPC, what users need most is not just a statement saying "we are very secure" but evidence that can be quickly verified—whether the audit scope covers critical modules, what the methodology is, whether risks have been mitigated, and if the information is consistently updated.
Furthermore, according to the OKX Wallet, after this upgrade, new audit reports and related information can be directly updated through configuration without the need for a new release. If this mechanism can operate stably in the long term, it effectively shortens the "externally verifiable" path, saving not only development and release costs.
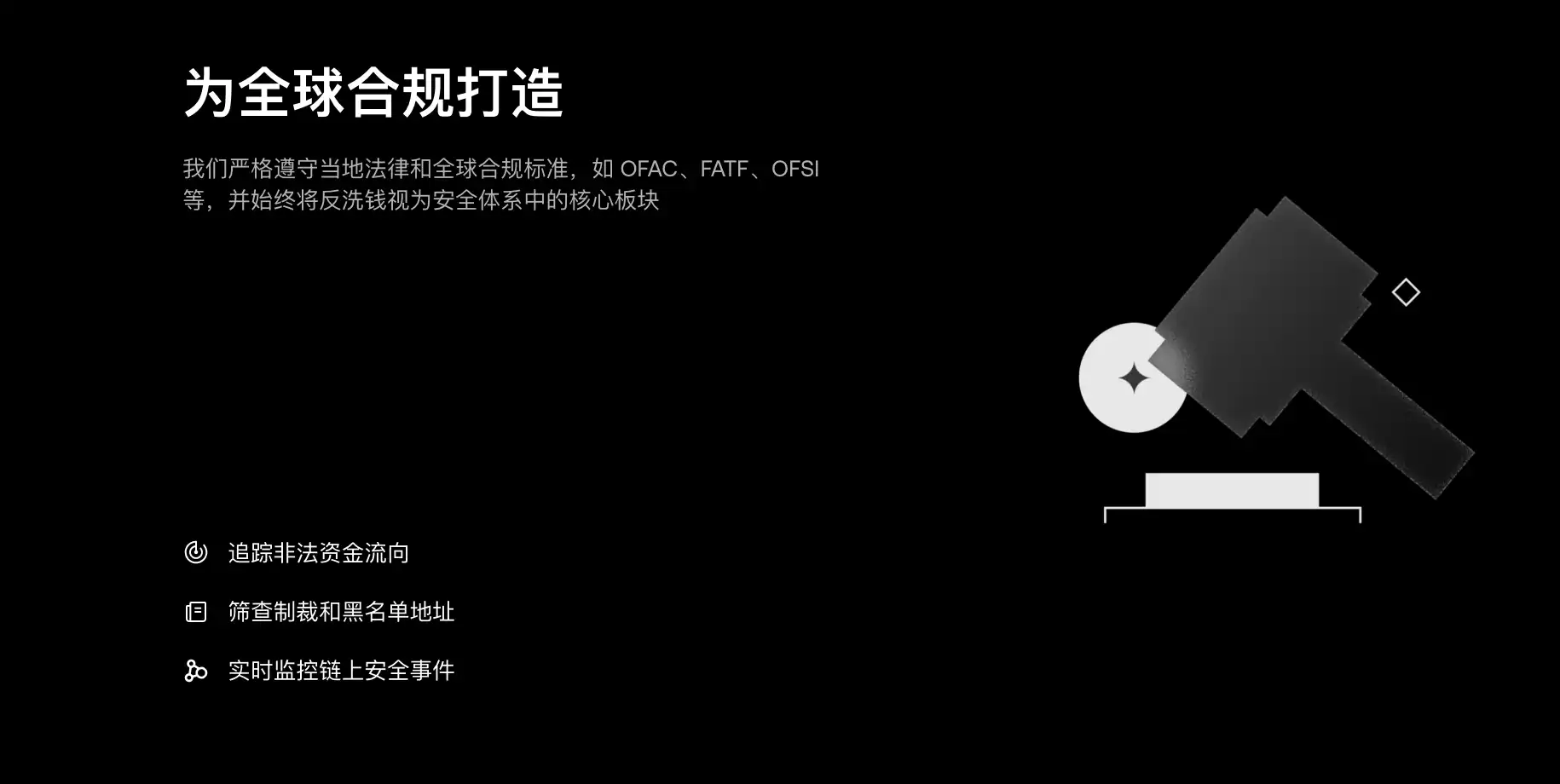
For users, this means that when an audit is added or completed, the public entrance can more quickly reflect the "latest status," reducing the uncertainty of "having to rely on forwarding screenshots/old links" during key risk windows. For third-party observers and researchers, it is easier to form a traceable timeline: which modules completed the audit when, what level of issues were discovered, when the fixes were confirmed and publicly updated. This turns "third-party endorsement" into a continuously auditable evidence chain, rather than a one-time display of a PDF.
This article is a contributed submission and does not represent the views of BlockBeats.
You may also like

From Wuhan to Silicon Valley, Manus did it in just nine months.
You may call it a “wrapper,” but it wrapped its way all the way to Meta.

How AI Helps Crypto Traders Analyze Markets, Manage Risk, and Trade Smarter
Crypto trading is no longer just about having a good idea—it is about executing consistently in a market that never stops. As data volumes and market speed increase, traditional manual analysis reaches its limits. AI helps traders move beyond these limits by transforming how markets are analyzed, how sentiment is interpreted, and how risk is controlled. This article explores how AI is reshaping crypto trading — and what that means for traders today.

WEEX Partners with LALIGA to Expand Global Reach and Integrate Crypto into Mainstream Sports Culture
Hong Kong, Jan. 1, 2026. WEEX has entered into a new partnership with LALIGA, as an official regional partner of LALIGA in Taiwan and Hong Kong. The agreement brings WEEX into LALIGA’s network of regional collaborators and opens the door to new ways of engaging both fans and traders during the season.

Hong Kong Virtual Asset Trading Platform New Regulations (Part 2): New Circular Issued, Has the Boundary of Virtual Asset Business Been Redefined?

AI Trading in Crypto: How Traders Actually Apply AI in Real Crypto Markets
Artificial intelligence has moved beyond experimentation in crypto markets. In 2025, AI-driven trading tools are increasingly used by traders who want better discipline, faster execution, and more structured decision-making in volatile markets. This guide explains how AI is actually used in crypto trading, step by step — with a focus on how these strategies are executed in real trading environments.

4 Years of Web3 Entrepreneurship: 7 Key Takeaways

Matrixdock 2025: The Practical Path to Sovereign-Grade RWA of Gold Tokenization

Caixin: Digital RMB Wallet Balances to Begin Earning Interest in 2026
Key Takeaways: Starting January 1, 2026, digital RMB wallets will earn interest on balances. The operational structure will…

From Failures to Success: Building Crypto Products That Truly Matter
Key Takeaways Building infrastructure in crypto doesn’t guarantee success; understanding user needs is critical. Products aimed at younger…

Cryptocurrency Trends and Insights: Navigating the 2025 Landscape
Key Takeaways Cryptocurrency continues to evolve rapidly, with new trends reshaping the market. Blockchain technology’s applications extend beyond…

Lighter: Airdrop Successful and Token Trading Imminent
Key Takeaways: The Lighter Discord community recently announced the successful distribution of LIT tokens, marking the beginning of…

The Eve of a Federal Pivot: Evaluating the Looming Change in the U.S. Central Bank
Key Takeaways Investors are gearing up for potential changes in Federal Reserve policy, with concerns about independence and…

6-Week, 3-Auditor Swap Sees Trump Crypto Firm Alt5 Sigma Mired in Financial Turbulence
Key Takeaways Alt5 Sigma, linked to the Trump family, faces financial reporting chaos and potential delisting risks due…

Yield Farming at 86% APY? How to Use Bots to “Earn While You Sleep” on Polymarket
Key Takeaways Polymarket presents untapped opportunities for bot utilization, despite existing competition. A proprietary trading bot streamlines the…

6-Week, 3-Auditor Switch Undermines Trump-Led Crypto Firm Alt5 Sigma
Key Takeaways Alt5 Sigma, tied to the Trump family, faces financial and operational turmoil marked by rapid auditor…

The Fed’s Monetary Policy Minutes and the Crypto Trading Insights
Key Takeaways The Federal Reserve is set to disclose the minutes from its recent monetary policy meeting, highlighting…

Unstable Stablecoins: Understanding the Market’s Concerns and Dynamics
Key Takeaways Recent financial reports indicate concerns and instability in the stablecoin market. Circle, a leading stablecoin issuer,…

MMA Completes $3 Million Private Sale to Develop Web3 Platform with Trump Jr.’s Investment
Key Takeaways MMA’s Strategic Funding Move: U.S. mixed martial arts firm MMA has successfully secured $3 million through…
From Wuhan to Silicon Valley, Manus did it in just nine months.
You may call it a “wrapper,” but it wrapped its way all the way to Meta.
How AI Helps Crypto Traders Analyze Markets, Manage Risk, and Trade Smarter
Crypto trading is no longer just about having a good idea—it is about executing consistently in a market that never stops. As data volumes and market speed increase, traditional manual analysis reaches its limits. AI helps traders move beyond these limits by transforming how markets are analyzed, how sentiment is interpreted, and how risk is controlled. This article explores how AI is reshaping crypto trading — and what that means for traders today.
WEEX Partners with LALIGA to Expand Global Reach and Integrate Crypto into Mainstream Sports Culture
Hong Kong, Jan. 1, 2026. WEEX has entered into a new partnership with LALIGA, as an official regional partner of LALIGA in Taiwan and Hong Kong. The agreement brings WEEX into LALIGA’s network of regional collaborators and opens the door to new ways of engaging both fans and traders during the season.
Hong Kong Virtual Asset Trading Platform New Regulations (Part 2): New Circular Issued, Has the Boundary of Virtual Asset Business Been Redefined?
AI Trading in Crypto: How Traders Actually Apply AI in Real Crypto Markets
Artificial intelligence has moved beyond experimentation in crypto markets. In 2025, AI-driven trading tools are increasingly used by traders who want better discipline, faster execution, and more structured decision-making in volatile markets. This guide explains how AI is actually used in crypto trading, step by step — with a focus on how these strategies are executed in real trading environments.
