Lurking in 600 Scam Groups, He Wants to Intercept Illicit Funds
Original Article Title: "Lurking in 600 Cyber Fraud Groups, He Aims to Intercept Illicit Funds"
Original Article Author: Sleepy.txt, Dongcha Beating
In business history, wherever wealth accumulates, there is always a tug-of-war between law and order.
Looking back from the tail of 2025, the global stablecoin issuance has stabilized at the $300 billion mark, nearly tripling from last year, with monthly transaction volumes reaching an astonishing $4 to $5 trillion. This cryptographic asset, stablecoin, has shed its "geek toy" label and has become the primary gateway for traditional finance to enter the digital world.
However, beneath the prosperity lies a hidden shadow. According to the latest industry report, the estimated scale of funds received by global illicit addresses in 2025 is set to exceed $51.3 billion. With hundreds of billions of funds able to cross borders in seconds, traditional regulatory measures often cannot keep up with this speed of flow, making it difficult to distinguish between legitimate business and criminal proceeds in real-time.
In this world where the rules have not yet fully formed, Professor Zhou Yajin is a special entrepreneur.
Zhou Yajin's career path is a typical epitome of an elite scholar colliding deeply with the industry. In 2010, he went to the United States to pursue a doctoral degree, delved into the field of mobile security for five years, and then joined Qihoo 360 with his mentor Professor Jiang Xuxian, completing the first leap from the laboratory to the industry front line. In 2018, he chose to return to Zhejiang University to take up the teaching reins. Three years later, he once again plunged into the industrial wave, founding the blockchain security company BlockSec.
Over the past four years, Zhou Yajin has led BlockSec to undergo a shift in business focus. Starting from initial smart contract code audits, it has gradually expanded into deeper areas such as security monitoring, fund tracing, and anti-money laundering compliance.
Zhou Yajin and his team have long been engaged in specialized research on on-chain data, and have even "lurked" in Southeast Asian cyber fraud and other underground groups, gaining a wealth of little-known underlying survival scenes. Through his perspective, we may be able to see the most authentic game of interests in this new digital world.
The following is Zhou Yajin's self-narrative, edited and organized by the Dongcha Beating editorial department after an exclusive interview.
This article is sponsored by Kite AI
Kite is the first Layer 1 blockchain built for AI agents, enabling autonomous AI agents to operate in an environment with verifiable identity, programmable governance, and native stablecoin settlement.
Kite was founded by AI and data infrastructure experts from Databricks, Uber, and UC Berkeley, has raised $35 million in funding, with investors including PayPal, General Catalyst, Coinbase Ventures, 8VC, and several top investment foundations.
From Code Auditing to the Anti-Money Laundering Battlefield
I pursued my Ph.D. in the United States from 2010 to 2015 under the supervision of Professor Jiang Xuxian. During that time, we focused on mobile security, particularly in the area of Android Malware detection, which was considered quite early globally. After graduating in 2015, I joined Qihoo 360 with my supervisor to commercialize our research.
In 2018, I joined Zhejiang University, transitioning back from the industry to academia. At that time, China was experiencing a small peak in the ICO craze in 2017 and 2018, bringing blockchain into the view of a small group of people. This is when I began to look into blockchain security. I noticed frequent on-chain security incidents back then, and while the academic community had many good solutions, the industry, on the other hand, was not doing well in addressing these issues; few were even paying attention to these problems.
Therefore, in 2021, Professor Wu Lei and I co-founded BlockSec.
Initially, people had a very stereotypical view of a "blockchain security company": Aren't you just doing audits? Indeed, we started with smart contract auditing. Due to our academic research background and our highly skilled team, we quickly established ourselves in the auditing business. However, from the perspective of founding the company, I did not want it to be just a cybersecurity service provider. Auditing addresses pre-launch security issues, but there were no particularly good solutions in the industry for post-launch protection at that time.
So in 2022, while continuing our auditing work, we also began developing an on-chain attack monitoring platform. Our initial product concept involved continuously monitoring on-chain transactions and automatically blocking any attack transactions. During this process, we found that despite audits and monitoring, project teams could still be attacked. Furthermore, with many phishing scams and end-user security incidents such as lost private keys where users lost money, new demands emerged.
When project teams were stolen from and users fell victim to phishing, they had to report the incidents and explain to law enforcement where the money had gone. Therefore, starting in 2022, we developed a funds tracking product, which is a fully SaaS-based product that users can subscribe to directly; we did not adopt a traditional B2B sales model.
After the launch of this product, we were surprised by the user profile. In addition to law enforcement agencies, media reporters, and financial institutions using it, there were even many freelance private investigators using it. These users from different backgrounds helped us refine the product during use, attracting more users. Coupled with our own attack detection engine, phishing detection engine, and more, these tags and data gradually solidified into our deepest moat.
A turning point occurred in late 2024 to early 2025.
At that time, the issuance of stablecoins began to skyrocket, and this market was no longer just Crypto Native individuals participating. Many traditional finance people started to enter the space, with their first encounter being with stablecoins. These individuals had a strong compliance awareness, and as soon as they entered, they would ask: If I want to use stablecoins, how do we address AML (Anti-Money Laundering) and CFT (Counter Financing of Terrorism) issues?
There was a lack of good compliance products on the market, and we happened to have accumulated three years of underlying tag data, so we quickly launched an anti-money laundering product. The whole process was actually quite natural; in response to market demand changes, we transitioned from a simple security service provider to a comprehensive "security + compliance" supplier.
Undercover
To do anti-money laundering, one must first have a deep understanding of how illicit funds are used.
From our research perspective, cryptocurrency crimes are usually divided into two categories: one is "crypto-native," such as code vulnerabilities targeting DeFi protocols, private key theft, or phishing. Without blockchain, these crimes would not exist at all.
The other category is "crypto-driven," such as online fraud, ransomware, and human trafficking. The emergence of cryptocurrency has greatly enhanced the efficiency and anonymity of their cross-border transfers. In these scenarios, what shocked us the most was the human trafficking in the Southeast Asian online fraud industry chain.
Many people feel that online fraud is far from them, but if you look at their job advertisements, the appeal is extremely precise: starting salary of 19,000 RMB per month, including plane tickets, room and board, and even solemnly promising to "must purchase Shenzhen social security." This type of fraud specifically targeting 18 to 37-year-old young people has deceived a large number of victims to cross borders and enter the fraud zones distributed in Myanmar, Cambodia, or Laos.

Today's online fraud zones have organizational structures as tightly knit as legitimate companies, with finance, technology, and call center teams all in place. To maintain this massive operation, they need to constantly replenish their "labor force," and the fraud zones (demand side) and human traffickers (supply side) do not know each other, with no trust in online communication whatsoever.
So, an intermediary emerged that specially endorsed illicit transactions, known as a "Labor Guarantor Platform."
The operation logic of this system is actually very similar to Taobao. The park first deposits a certain amount of USDT as a guarantee on the platform; the trafficker is responsible for luring the victim across the border and delivering them to the designated "inspection" location. After both parties confirm in a Telegram private group that everything is correct, the platform will release the deposit to the trafficker. The transaction principle followed is "Goods received, payment settled." If either party tries to default, the platform will freeze or confiscate the deposit according to the rules to compensate the other party.
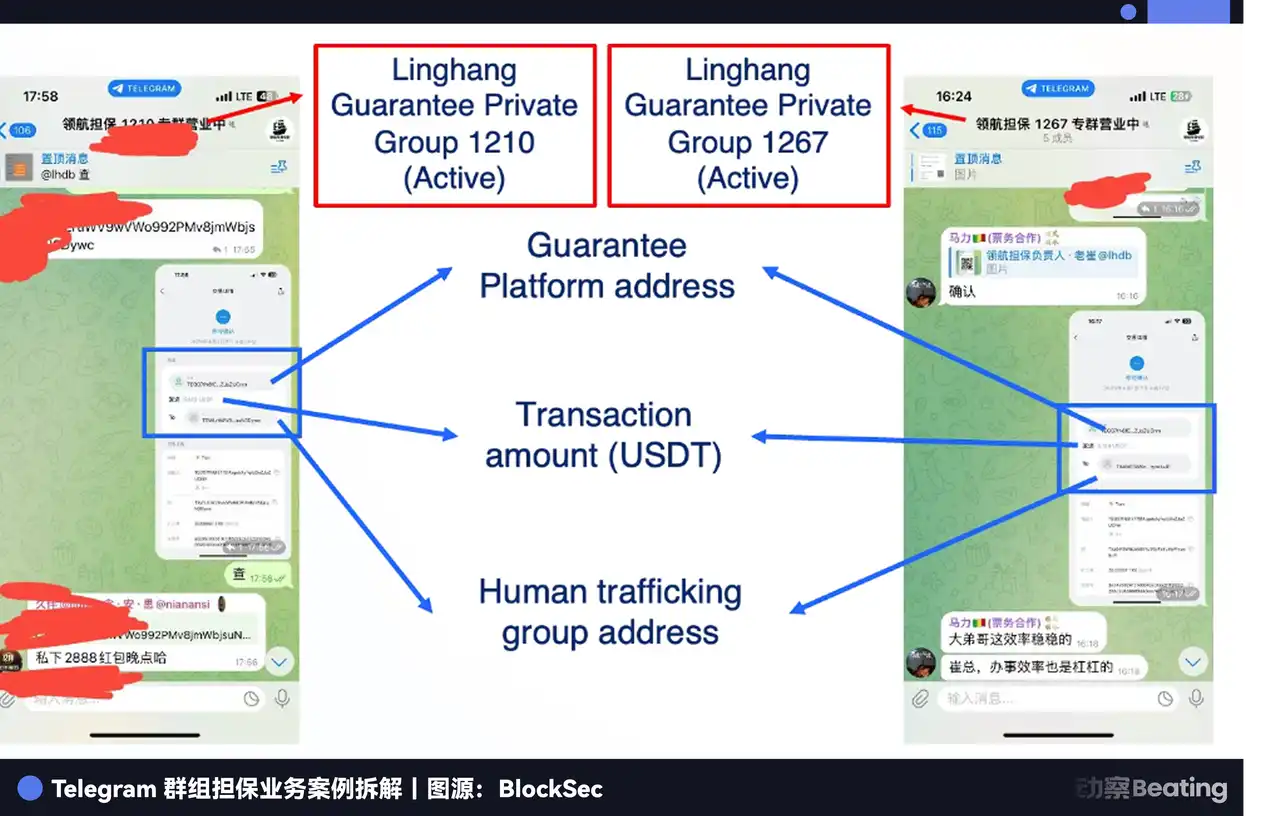
To attract business, these platforms will showcase their strength in public Telegram channels. For example, in the navigation guarantee or Haowang guarantee channels, system bots will instantly post screenshots of transactions and on-chain transfer records. They will even run promotions like a regular e-commerce platform, such as commission collection on behalf, or buy 10 get 2 free.
This is also the most direct point of observation for us to analyze the dark industry.
From February to August 2025, we developed an automated system that continuously lurked in these groups to gather intelligence. As the chats in the groups were filled with jargon, we specifically trained a large language model for analysis.
In the dark industry jargon, the victim is called "Fish," and the scam routine and victim information are referred to as "Material." The granularity of Material is detailed, including "Triple black material," "Mixed material," "Airplane ticket material," etc. Based on the money laundering process, it is further divided into "First-order Material," where money is directly received from the victim, and "Second-order Material" that undergoes layered processing.
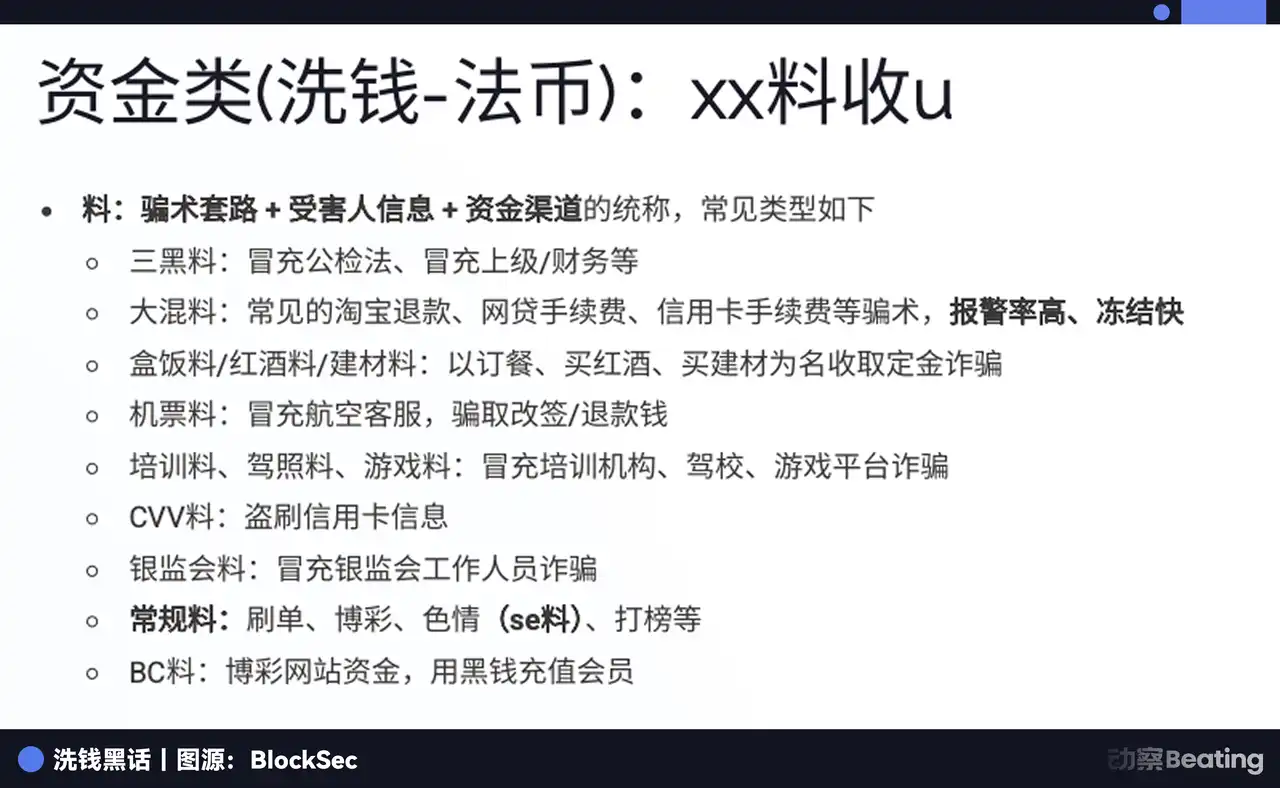
There is also a job called "Mobile Access," where domestic accomplices use audio cables or specific apps to reroute overseas scam calls to domestic mobile phones to bypass the telco's anti-fraud interception. They can earn about 200 USDT per hour doing this. They have recruited many young people from small towns to do this job.
In these dark industry groups, there is even widespread dissemination of the "Anti-Police Tutorial," meticulously guiding everyone on how to calmly deal with investigations, such as insisting on reporting a lost phone, deleting scripts and encryption communication apps in advance. The tutorial ends with a very ironic sentence—"Salute to every hardworking individual."
Through six months of automatic monitoring, for one of the guarantor platforms, we have identified a total of 634 addresses associated with a human trafficking group, tracking nearly $12 million in illegal transaction amounts. At the peak of its activity, ten people were trafficked into the park through this one guarantor platform every day. The actual situation may be more severe due to the existence of other guarantor platforms.
When tracking the fund flow, we found that the majority of these funds are on the Tron chain, mainly using the USDT stablecoin. Due to Tron's low barrier to entry and cheap transaction fees, it is very suitable for these low-tech criminal groups. Although Tron's transaction fees have now increased, they have already developed a usage habit making it difficult to switch to other methods.
We analyzed the fund flows of more than 120 criminal groups and found that over 34.9% of these illicit proceeds ultimately flowed into OKX's hot wallet, 6.9% into Binance, and 14.4% into Huobi-related hot wallets.
When you can see how this money came in and where it flowed, anti-money laundering is no longer an empty phrase. This real data brought back from the grassroots group is the most critical barrier to security and compliance.
12 Seconds: The "Sniper" Hacker in the Mempool
In the security industry, there has always been a knot: auditing can only ensure that the code is secure at the moment of deployment. But once the project is up and running, it faces round-the-clock global hackers. If auditing is "static defense," can we find a way to do "dynamic interception"?
In 2022, while conducting audits, we launched an on-chain attack monitoring platform. The underlying logic of this product is to monitor Ethereum's Mempool. You can think of the Mempool as a waiting room where all transactions must line up before being officially packaged into a block and recorded in the ledger.
In this waiting room, we not only monitor regular user transactions but also transactions with attack characteristics. Once a suspicious transaction that appears to be an attack is detected, our system immediately initiates automatic analysis in a private chain environment: What does it want to do? Does the logic hold? How much money will it steal?
The most thrilling game usually happens in a mere 12 seconds.
After the Ethereum merge, the block time has been fixed at 12 seconds. This means that from the moment a hacker issues an attack command to when this transaction is actually packaged and confirmed, there is an extremely brief window of time. These few seconds are the golden rescue time given to the white hats.
After confirming an attack, our system automatically generates a "front-running" transaction. The content of this transaction is almost identical to the hacker's, but the crucial difference is that we change the receiving address of the funds from the hacker's wallet to our predefined secure address.
To outpace the hacker, we must obtain priority in getting the transaction included in a block by the miner.
Hackers, in order to maximize profit, usually set a standard Gas Fee. We, on the other hand, leverage an algorithm to significantly increase the Gas Fee, even directly tipping a portion of this money to miners. Driven by self-interest, miners prioritize including our transaction in a block. Once our transaction successfully goes through, the hacker's transaction is automatically invalidated.
This capability has saved the lives of many projects in real-world scenarios.
One of the most notable instances was when we successfully front-ran an attack on a protocol in the mempool, single-handedly rescuing 2909 ETH for the project team. At that time, the hacker had already exploited a vulnerability, on the verge of making off with tens of millions of dollars. Our monitoring system instantly triggered an alert, and within seconds, we completed attack simulation, transaction generation, and Gas bidding. In the end, that substantial sum was transferred to our secure address ahead of the hacker.
In the past, project teams who fell victim to theft could only resort to posting pleas on Twitter or negotiating with the hacker to see if they would return the funds for a bounty. However, now, through technological means, we intercept the funds forcibly the second before the hacker succeeds.
Only by understanding code better than the hacker and running faster than the hacker can you hold the final line of defense in this "Code is Law" dark forest.
Afterword
If the past decade in the crypto world was a "Gold Rush," then standing at this 2025 milestone, what we see is a return to "certainty." As the stablecoin market cap surges to 300 billion dollars, as a digital new financial system transitions from the "wilderness" to the "city-state," technology is no longer just a lever for wealth accumulation; it must first and foremost become a shield against the darkness of human nature.
The transformation experienced by Zhou Yajin and his team is fundamentally a reflection of this business logic. From code audits to dynamic interception, and then to deep dives and dismantling of illicit chains, this is not the solitary valor of an individual, but a defense mechanism that emerges inevitably as technology evolves to a certain scale. In this world where code equals law, if the chronic issues of illicit fund flow and security vulnerabilities are not addressed, then the so-called "financial revolution" can only ever remain a game for a few.
In the annals of business, any industry that has gone mainstream has undergone the throes from chaos to the rule of law. Perhaps this is a long and tedious process, but just as Zhou Yajin said, the ultimate form of security is "unnoticeable."
Only when security becomes as ubiquitous as air yet ignored by all can this once volatile digital frontier truly complete its pioneering civilization.
You may also like

CoinDesk 20 Performance Update: Uniswap (UNI) Dips 1.5% as Index Experiences Downturn
Key Takeaways Uniswap (UNI) experienced a notable drop of 1.5% as the CoinDesk 20 Index saw a decline.…

Crypto Markets Today: Bitcoin Slides as Asia-Led Sell-Off Hits Altcoins
Key Takeaways: Bitcoin could not surpass the $94,500 mark and fell to roughly $91,530, contributing to a wider…

Start-of-the-Year Crypto Rally Stalls: What’s Next?
Key Takeaways The initial crypto market boost at the start of 2026 has lost momentum, primarily due to…

Barclays Invests in Stablecoin Settlement Firm as Tokenized Infrastructure Expands
Key Takeaways Barclays has invested in Ubyx, a U.S.-based startup focused on developing clearing systems for tokenized forms…

Karatage Welcomes Shane O’Callaghan as Senior Partner in Strategic Move
Key Takeaways Karatage, a London-based hedge fund, appoints Shane O’Callaghan as a senior partner to enhance its institutional…

Lloyds Bank Achieves a Milestone: UK’s First Gilt Purchase via Tokenized Deposits
Key Takeaways Lloyds Bank executed the first-ever UK government gilt purchase through tokenized deposits, highlighting a transformative use…

Morgan Stanley Files for Ether Trust after Bitcoin and Solana ETF Proposals
Key Takeaways Morgan Stanley has made a significant move by filing for an Ethereum Trust with the SEC,…

JPMorgan Targets Canton Network for Next Phase of JPM Coin
Key Takeaways JPMorgan’s Kinexys unit is set to advance the use of JPM Coin by integrating it with…

2025 Crypto Bear Market: A Crucial Year for Institutional Repricing
Key Takeaways The 2025 crypto bear market witnessed significant corrections in the DeFi and smart contract sectors, setting…

Trend Research: 2026 Beyond Paradigm, WLFI Initiates Financial Ecosystem New Era

Six-Figure Target: The Top Airdrops to Watch in 2026

The US has had a president impeached twice, and Trump's platform says it's not an "insurrection."

2025 Crypto Card Annual Report: 40,000 Monthly Active Users, Average Spending of Less Than $100

2026 Crypto New Year's Rally: Cautiously Bullish Market Sets Sail

A “sexy casino,” where real-estate speculation has moved online.
Using Polymarket to predict U.S. home prices feels eerily reminiscent of the 2008 subprime mortgage crisis.

Why AI Tokens Are Rising Faster Than the Broader Crypto Market
AI tokens are outperforming — and not quietly. Bitcoin is moving. Ethereum is holding ground. Yet some of the strongest relative gains are coming from AI-labeled tokens, not majors, not memes. At first glance, this feels intuitive. AI is real technology. It’s shaping industries far beyond crypto. But markets rarely move on intuition alone — especially not this fast. When prices accelerate ahead of adoption, the more useful question isn’t “Is AI important?” It’s which version of the AI story the market is buying — right now.

Privacy Lane, a16z's Key Trends for 2026

After Lighter, the next batch of Perp DEXs Worth Keeping an Eye On
CoinDesk 20 Performance Update: Uniswap (UNI) Dips 1.5% as Index Experiences Downturn
Key Takeaways Uniswap (UNI) experienced a notable drop of 1.5% as the CoinDesk 20 Index saw a decline.…
Crypto Markets Today: Bitcoin Slides as Asia-Led Sell-Off Hits Altcoins
Key Takeaways: Bitcoin could not surpass the $94,500 mark and fell to roughly $91,530, contributing to a wider…
Start-of-the-Year Crypto Rally Stalls: What’s Next?
Key Takeaways The initial crypto market boost at the start of 2026 has lost momentum, primarily due to…
Barclays Invests in Stablecoin Settlement Firm as Tokenized Infrastructure Expands
Key Takeaways Barclays has invested in Ubyx, a U.S.-based startup focused on developing clearing systems for tokenized forms…
Karatage Welcomes Shane O’Callaghan as Senior Partner in Strategic Move
Key Takeaways Karatage, a London-based hedge fund, appoints Shane O’Callaghan as a senior partner to enhance its institutional…
Lloyds Bank Achieves a Milestone: UK’s First Gilt Purchase via Tokenized Deposits
Key Takeaways Lloyds Bank executed the first-ever UK government gilt purchase through tokenized deposits, highlighting a transformative use…

